User attributes in the SAML assertion
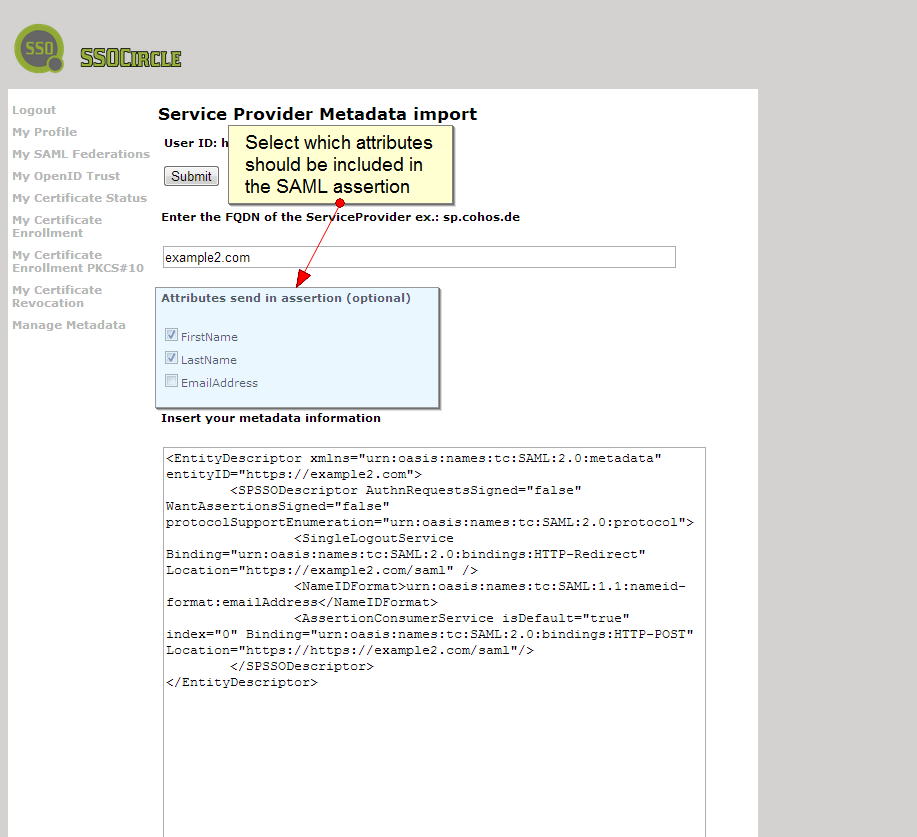
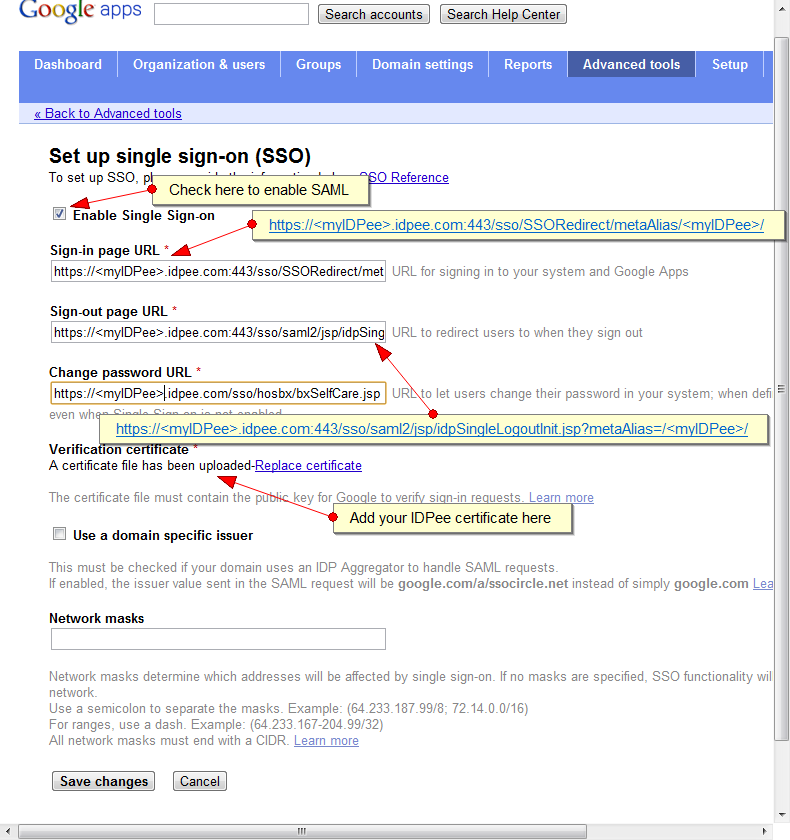
It is nothing really new, but it was a missing feature in the administration GUI of our Public IDP: Configuring which user profile attributes should be sent as an AttributeStatement in a SAML assertion.
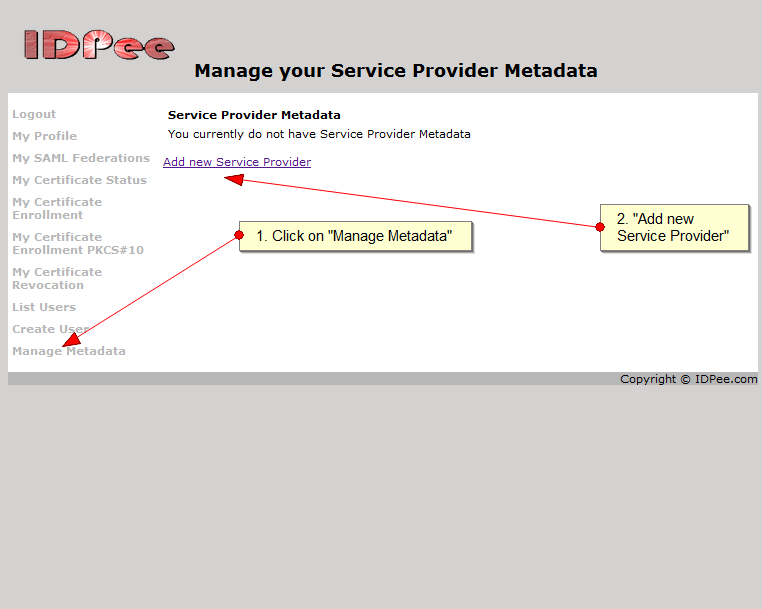
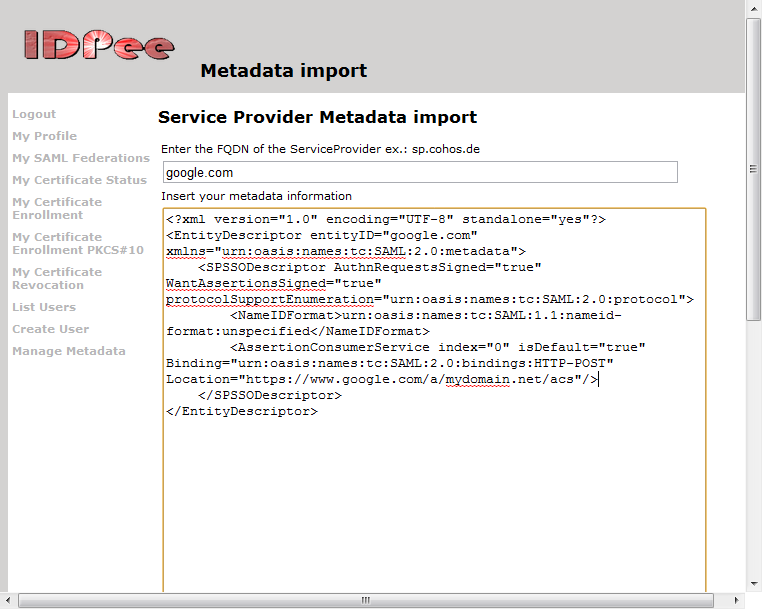
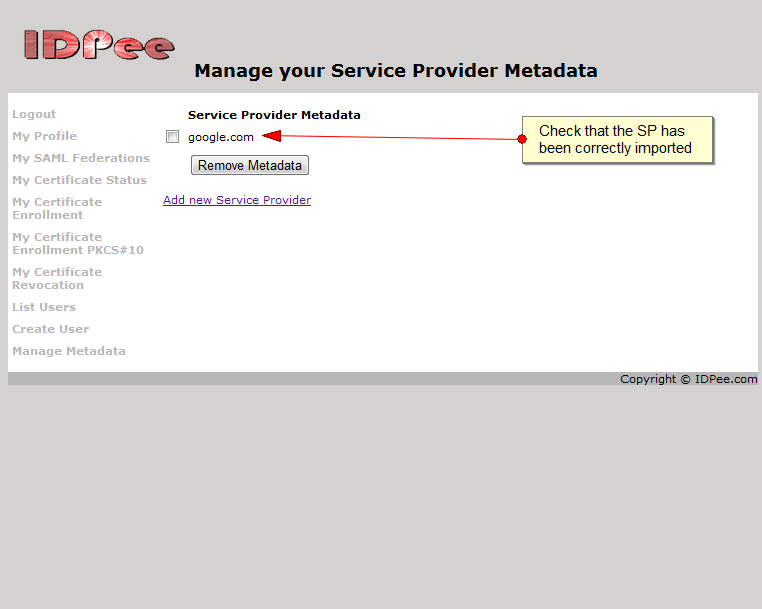
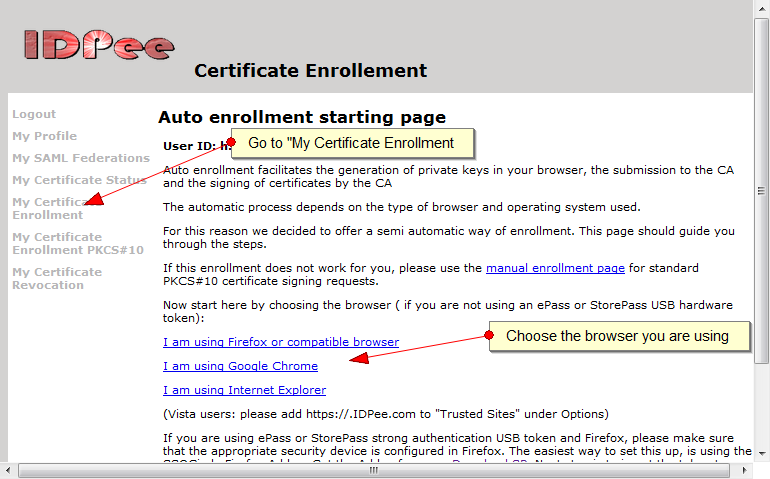
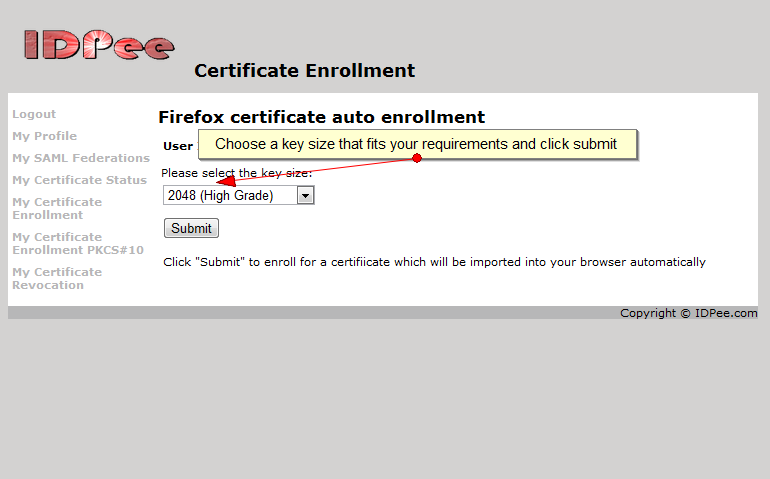
The feature has always been there, but administrators had to open a service request to have attributes configured. Now, you can select which attributes to insert during importing of Service Provider metadata. A sample is in the screen shot below: