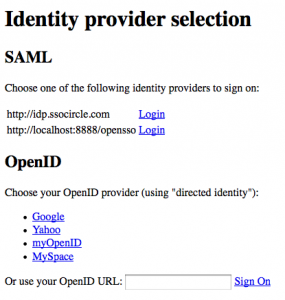
frrry is using SSOCircle as Identity Provider
Ferry Meewisse, a dutch bag designer, who runs the web site frrry.com, bags & fashion accessories, is using SSOCircle as a login option for partners and employees.
Beside Google, Yahoo!, MySpace.com, myOpenID and generic OpenID, they have the option to log in via SSOCircle and leverage several strong authentication options like X.509 certificates, USB tokens and OTP options like Yubikey or Swekey.