Authorization as a Service
SSOCircle Entitlement Service =
- ReBAC + ABAC + RBAC = StarBAC
- XACML + JSON + REST = API
- OAuth = Authentication
- AzaaS = Service
- MyIdentityGraph Ontology = Innovation
SSOCircle MyIdentityGraph introduces a new Authorization as a Service (AzaaS) functionality with *-BAC ( StarBAC) support. StarBAC can be described as a super-set of various access control principles like ABAC, RBAC and, with a strong emphasis, ReBAC (Relationship Based Access Control).
ReBAC considers the relationships stored in the Graph database “MyIdentityGraph” to deduct access permission information by leveraging Graph algorithms.
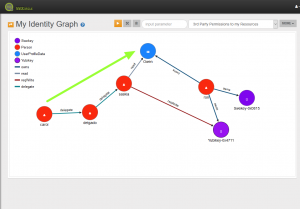
An example is provided in the image below. Throughout our use cases we will use the following actors.
The question is: “Has Carol read access to Ron’s UserProfileData”.
A graph traversal algorithm is used to find a permission path from the person node Carol to Ron’s UserProfileData. And if such a path exists the policy decision point returns “PERMIT” otherwise a “DENY” is returned.
The API to establish such a service must be based on a standard. But being standardized is no sufficient, a usable and accepted access protocol is needed. XACML paved the way but still lacks brought acceptance. With XACML JSON Profile request and response interface the situation will be improved. But there is more to AzaaS than just asking for a permit or deny. MyIdentityGraph supports requesting and approving permissions by end users to resources owned by another person. This enables a resource owner to control permissions and sharing of his resources.
SSOCircle MyIdentityGraph combines a Graph representation of Identities, a XACML JSON Request/Response based ReBAC authorization service (AzaaS), and OAuth standard based communication protocols.
More details about the MyIdentityGraph Ontology, AzaaS and ReBAC can be found in the Knowledge Center.
MyIdentityGraph is currently in Beta but integrated in the SSOCircle Public IDP. Registered SSOCircle Public IDP user have access to it at MyIdentityGraph and can access the REST API of the entitlement service.