X.509 Certificate generation and keygen
Background: In SSOCircle Public IDP we provide client certificates as a mean of strong authentication. For more than 10 years we offer PKI functionality to ease the generation of private/public key pairs as well as generate and enroll X.509 certificates. In the past most browsers supported CertEnroll / Xenroll Active X to complete the key generation tasks.
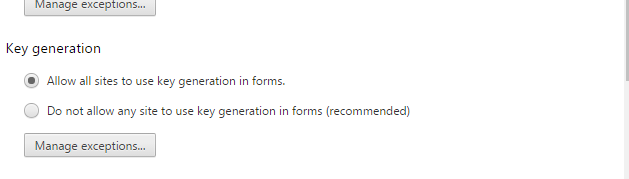
Back in 2016 we blogged on the vanishing support of the <keygen> HTML element in Chrome Browser as of version 49. From that time keygen was only working after modifying some privacy settings.
As of today, the current support across the major browsers has almost completely faded away. The following table lists the status as of now (for desktop OS).
 |
Firefox keygen support ended as of version 69 (September 2019) |
 |
Chrome keygen support ended as of version 57 (March 2017) Limited support as of version 49 |
 |
Edge no support for keygen or CertEnroll |
 |
IE supports CertEnroll Active X |
 |
Safari 1.2+ keygen supported |
 |
Opera 3+ supports keygen |
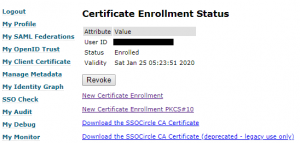
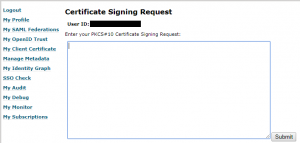
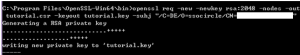
We have recently got a lot of feedback about the missing PKI functionality in the SSOCircle public IDP. From the beginning we provided a #PKCS10 certificate creation form to enroll and bind the certificate to the user. Creating keys manually with the correct subject was tedious and error prone. Thanks to our user Ming Yu who provided a tutorial of how to enroll the certificate and avoid pitfalls, many users were able to manage that part. But many users were still missing the automatic enrollment by just simply clicking the “keygen” button.
So, what’s next: We have now modified the fuctionality to generate RSA key pairs, create and enroll the certificate by the virtue of a click … and a manual import step into the certificate manager …
As #PKCS12 files are supported by all certificate managers/browsers/OS we think we provide a way which supports all.
Details can be read here. Go and test it at the Public IDP