SAML SSO to Amazon AWS from SSOCircle
Many people were asking about doing SSO to Amazon AWS from SSOCircle. Since SSOCircle Public IDP has a common Circle of Trust the Service Provider EntityIDs are shared and must be unique.
AWS provides a single SAML Service Provider Metadata file at https://signin.aws.amazon.com/static/saml-metadata.xml for all AWS customers. As the AWS SP is already imported into the Circle of Trust, the EntityID specified in the Metadata file is already taken. The next user importing the same Metadata will get the error:
A urn:amazon:webservices entity already exists. Go to the *Manage Metadata*, and delete the existing urn:amazon:webservices entity first
As the SP is bound to another user, it is not possible to delete the SP.
The good thing is, because the AWS Metadata is already trusted, the import step can be skipped.
The bad thing is, that every AWS user who configures trust for SSOCircle accepts SAML assertions from any user logged in to the Public IDP. If someone knows or guesses the Role ARN of another AWS instance this is potentially dangerous. Because of this we do not expose the configuration of the AWS Role in the GUI. Instead Premium subscribers can open a ticket for that.
NOTE: This does not apply to hosted IDP’s (IDPee) instances who do have individual Circle of Trust and Metadata. These are fully configurable via the GUI for AWS
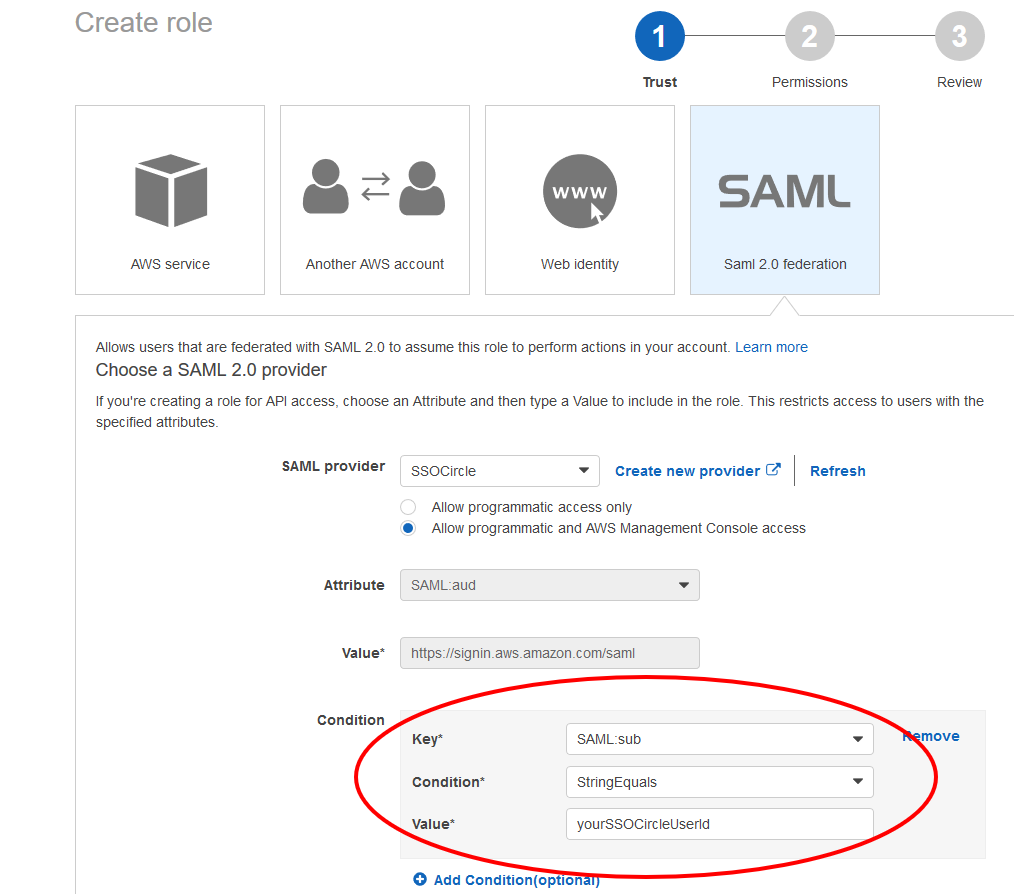
For users who go with the SSOCircle Public IDP and AWS, we strongly recommend to further restrict the access for SAML to AWS with additional conditions:
Follow these steps of configuring the IDP and create a Role with at least the following condition. Change yourSSOCircleUserId to the value of your SSOCircle username.