OpenID Configuration
This page describes the use of OpenID Connect with your IDPee instance. OpenID Connect builds upon the OAuth 2.0 framework and adds an identity layer to it. Most explanations in this document applies analogous to OAuth 2.0 applications.
Note: In URLs and descriptions please replace <YOUR_IDPEE>.idpee.com with the name of your hosted instance.
Quick Start:
OpenID Connect defines standard formats to retrieve configuration information:
https://<YOUR_IDPEE>.idpee.com/.well-known/openid-configuration
Example for the information stored under this URL:
{
"issuer": "https://<YOUR_IDPEE>.idpee.com:443/sso",
"authorization_endpoint": "https://<YOUR_IDPEE>.idpee.com:443/sso/oauth2/authorize",
"token_endpoint": "https://<YOUR_IDPEE>.idpee.com:443/sso/oauth2/access_token",
"userinfo_endpoint": "https://<YOUR_IDPEE>.idpee.com:443/sso/oauth2/userinfo",
"id_token_signing_alg_values_supported": ["RS256", "HS256","HS512","HS384"],
"jwks_uri": "https://<YOUR_IDPEE>.idpee.com:443/jwks.json",
"response_types_supported": ["code", "id_token","token id_token"],
"claims_supported": ["email","profile"],
"subject_types_supported": ["public"],
"version": "3.0"
}
| Property | Description |
| issuer | The URL identifying the issuer of tokens. The same value as the iss claim |
| authorization_endpoint | URL of the OpenID Provider ‘s OAuth 2.0 Authorization Endpoint |
| token_endpoint | URL of the OpenID Provider ‘s OAuth 2.0 Token Endpoint |
| userinfo_endpoint | URL of the OpenID Provider ‘s UserInfo Endpoint |
| id_token_signing_alg_values_supported | JSON array containing a list of the JWS signing algorithms (alg values) supported by the OpenID Provider for the ID Token to encode the Claims in a JWT |
| jwks_uri | URL of the OpenID Provider ‘s JSON Web Key Set |
| response_types_supported | JSON array containing a list of the OAuth 2.0 response_type values that this OpenID Provider supports |
| claims_supported | JSON array containing a list of the Claim Names of the Claims that the OpenID Provider MAY be able to supply values for |
| subject_types_supported | JSON array containing a list of the Subject Identifier types that this OpenID Provider supports |
The above configuration refers to the JWKS_URI which contains the signing key(s) the Relying Party uses to validate signatures from the OpenID Provider.
https://<YOUR_IDPEE>.idpee.com/jwks.json
An example of the jwks.json document is:
{
"keys": [{
"kty": "RSA",
"e": "this is the exponent",
"use": "sig",
"kid": “this is the identifier",
"alg": "RS256",
"n": "this is the modulus"
}]
}
| Property | Description |
| kty | Key Type Parameter The “kty” (key type) parameter identifies the cryptographic algorithm family used with the key, such as “RSA”. |
| e | Exponent |
| use | Public Key Use Parameter: The “use” (public key use) parameter identifies the intended use of the public key. |
| kid | Key ID Parameter: The “kid” (key ID) parameter is used to match a specific key |
| alg | Algorithm Parameter: The “alg” (algorithm) parameter identifies the algorithm intended for use with the key. |
| n | Modulus |
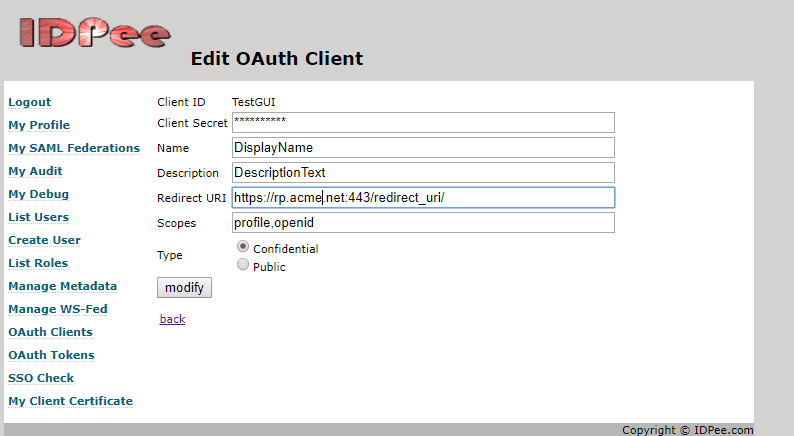
You can create and edit OAuth clients in the Admin GUI under: “OAuth Clients”
You can view the OAuth Tokens in the Admin GUI under “OAuth Token”.