Impressions from European Identity Conference 2011
This year’s European Identity Conference (EIC2011), a fixed star in the digital identity world took place in Munich, Germany, from 10.-12. May and a supplemental workshop day on the 13th. As last year the conference also hosted the Cloud 2011. In terms of venue the conference made a leap into the future from the venerable Deutsche Museum to the Dolce Ballhaus-Forum, a modern hotel and conference center north of Munich. Needless to say that the conference was well organized by KuppingeCole and newly introduced supplemental offerings like the World Cafe unconference or a crash course in international privacy and IT security law.
Before diving into details my overall impression was that the identity community is finally reaching a state of reflection. Compared to last year, where I experienced a more enthusiastic atmosphere and speakers, the 2011 conference was strongly influenced by academics and organizations. Keynote topics like “where will identity be next year” and personal changes like that of Kim Cameron who recently left Microsoft inspired Jackson Shaw to present a retrospect bolstered thoughtfulness.
In addition the human part of identity is coming more and more into consideration. At EIC2011 we had the chance to listen to speakers like Emilio Mordini, a psychoanalyst and founding director of Centre of Science, Society and Citizenship or Stephan Humer, a sociologist from Berlin University of Arts whose presentations demonstrate that sociological aspects play a very important role in acceptance and success of digital identity and internet security.
We finally reached the social human being and not only the user account. 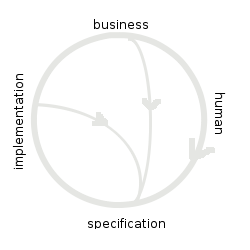 identity acceptance development cycle, shown below, demonstrates these iterations which might lead to new rethinking and specifications.
identity acceptance development cycle, shown below, demonstrates these iterations which might lead to new rethinking and specifications.
This is a great achievement. In other areas it seems we are not at that point yet. Looking at the evolution of OpenID which is finally approaching a new level with OpenID Connect reinventing the wheel that SAML 2.0 already did but with less complexity replacing SOAP and XML security with REST and JSON. That looks to me like taking the first shortcut in the identity acceptance development cycle due to missing implementation acceptance at least in the consumer identity space. Listening to Barbara Mandl from Daimler revealed that there are also several instances of shortcut 2 caused by business not technical reasons. In summary there is still a lot to do for the identity community, despite that most technologies are mature, the digital identity in a social world is very complex and subject to change.
In my eyes the most dynamic fields are:
- OpenID Connect
- OAuth 2.0
- XACML 3.0
- SCIM
the integration of mobile devices as a whole and the formation and establishing of Trust Frameworks.
But continuing with details of the conference in chronological order. As always it is subjective due to my interests and the selection of presentations visited.
Day 1:
Preconferences:
The conference started similar to the years before with a set of preconferences. One of these was an update and overview of OpenID staffed with Eric Sachs, Google, David Recordon, Facebook, John Bradley, Nat Sakimura and Don Thibeau, OpenID Foundation, Mike Jones and Anthony Nadalin, Microsoft; The upcoming version of OpenID is expected for IIW in November and will be named OpenID Connect, the AB for artifact binding will be removed from the name. It’s goal is to make “easy things easy and harder things possible”. Its design is modular with focus on integrating mobile devices. It will replace the 3.5 years old OpenID 2.0 spec and will introduce some advanced concepts known from the SAML spec, like level of assurance similar to SAML auth context and session management, like single logout, but less ambitious than the one known from SAML 2.0. OpenID connect is based on OAuth 2.0 which itself will be finalized in the next months.
Announcements:
In a press conference Drummond Reed, known from his work on XRI, XDI, Information Card, OIX and OpenID foundation, launched a new start-up called connect.me. Connect.me is the first personal respect trust network in which you can vouche/vote for a person in a specific respect. With joining the network people agree to 5 principles called promise, permission, protection, portability and proof. Connect.me is not a new social network but constitutes a layer above other social networks. By vouching for a person at http://vote.connect.me you are giving a person “trust points” for a specific respect. For me this is comparable to the seller rating in ebay. I am curious to see how this will develop and if we all get personal ratings in the new future. I expect that in next year’s EIC agenda there will be the rating mentioned right behind the speaker’s name. We will see if leaving Microsoft will change Kim Cameron’s rating from AAA to AAA+ or AAA-.
Keynotes:
As usual Martin Kuppinger gave the opening notes with an overview on the the hottest topics which are:
- Cloud Computing
- Information Security
- Business-driven service management (far more than ITIL)
- Make BYOD secure
BYOD stands for “bring your own device” and reflects that many employees nowadays want to use their own private devices (iPad, iPhone etc) in business. This poses a new thread on corporate security.
Cloud: In cloud computing more standards will evolve and there will be no success without security. Recent security breaches like SONY or Amazon give us a new awareness of users, company CIOs and politics that accelerates the development.
GRC: continuing progress towards one GRC for business and IT. Regulatory pressure will reach other industries.
IAM: PxM, privileged x=(Access,Account,Identity, User) Management, is the important topic in 2011. Externalization of authorization is becoming reality and versatile authentication will become more widespread. The RSA breach as one of the reasons.
Mobile:
BOYD as a new phenomena and the circumstance that the built-in security is not sufficient. Kuppinger compared the security of mobile devices to the security standard of PC in the 80s.
CIO key topics in 2011 will be
- How to make the cloud part of the IT
- How to enforce and privacy protect data (SONY)
- How to reach enterprise GRC maturity
- How to reach governance
- How to optimize investments and close gaps
- How to improve information security
First day keynotes on “the future of identity” continued with presentations by Laurent Liscia, executive director of OASIS, Wolfgang Hirsch of Siemens IT solutions, Maurizio Griva of Reply. Kim Cameron’s keynote was canceled and replaced by an interview in which Tim Cole eagerly tried to get information about Cameron’s real reasons for leaving Microsoft. Was it Microsoft’s recent strategy? No answer from Cameron except a comment expressing his feelings: “hey man, I am feeling so free”. Jackson Shawn (Quest Software) keynote directly influenced by Cameron’s “retirement” gave a retrospective of the development of identity from 1991, 1996, 1999 and a forecast how it may look like in 10 years from now. Illustrated with photos from Cameron and him as they were close fellows all these years. Shawn said that the start-up companies he is watching right now are Oka, Biznet3, SecureAuth and Symplified.
Prof. Reinhard Posch, CIO for the Austrian Government, presented on eID cards and the cloud and Jörg Asma from KPMG gave his view on future hot topics: Facebook as an identity manager and application hoster. Cloud computing driven by the use of devices like iPad etc. BYOD, the use of private devices for business purposes. Interesting his statement from HR on attracting new talent: today you don’t need a fancy car to attract new hires but cool lifestyle devices like the iPad or iPhone.
Day 2:
Starting with three keynotes from Dave Kearns on integrated identity management, Rolf von Rössing, VP of http://isaca.org. ISACA is an independent , nonprofit, global association, ISACA engages in the development, adoption and use of globally accepted, industry-leading knowledge and practices for information systems. Framework examples are: Cobit 5 bringing the GRC frameworks to the public, Risk IT, Val IT and BMIS. Professor Eberhard von Faber presented on froward strategies to protect corporate data in the cloud: Encryption is important to protect data in the cloud but has its limitation in server side batch processing for example in BI systems.
Alternatives are homomorphic encryption, not now but maybe in 10 years, or peudonymisation which can solve some problems. [Remark: fully homomorphic encryption is a encryption in which a service provider can operate (add, multiply) on the encrypted data without being able to decrypt data. That means a cloud service can work on data without knowing it.] Other means to secure the data are database encryption and database activity monitoring. Access restriction only protects from outside. Most service provider lack in protection from inside attacks. Limiting access to data (e.g. by terminal server or not having full access to “data files”) and EDRM (enterprise data right management) as well as VPN against eavesdropping and protection against access of data from other tenants are important. Securing the cloud isn’t easy. It still need to be easy to use. User awareness, control and monitoring are key for successful cloud deployments.
Breakout:
The conference offered four parallel tracks from which I selected the Directory & Federation track. Martin Kuppinger gave an introduction with the statement: you cannot make federation which relies on data quality if you do not have your directory in order. Federated directories are a solution to that problem as the single directory does not work due to complexity and privacy. Here comes virtual directories or cloud directories into play, whereas use cases for the latter are authentication of customers, directories for specific applications or the migration of in house directories to the cloud. Kuppinger expects directories in 2020 being similar as they are today.
I was surprised seeing an overcrowded room when visiting “How to authenticate for the cloud”. A panel discussion lead by Sebastian Rohr with Judith Little, CloudID, Mark O’Neill, Vordel, Travis Spencer, Ping, and Tom Stewart, SecureAuth. The better way to do the authentication to the cloud is to authenticate internally and then federate to outside. This will increase adoption as too much different methods lack user acceptance. Authorization to the cloud is still difficult to handle as there are mainly proprietary methods used.
“Federation lessons learned” with Matthew Gardiner, CA & Kantara, Nishant Kaushik, Oracle and Travis Spencer, Ping, concluded that federation is now main stream. Success of facebook connect demonstrates that federation still profits from the federated SSO use cases but that reinventing over and over with new technology is problematic. A business sponsor and a aligned strategy is needed. One question asked by Mike Small was if there is a reason to not use federation. Spencer answered that there is no reason except there are some use cases for mobile devices with limited capability that can be overcome by OAuth or WS-*. Cloud business becomes a major driver for federation which does not stop at SSO. Provisioning, authorization and audit are getting more and more important.
Cloud standards adoption track: in the absence od Laim Lynch, eBay, Mike Small gave an introduction to the topic. Analyzing the risks in cloud computing. Starting with the risk of vendor locking which is more prevalent with SaaS than with PaaS or IaaS. Other risks are “Legal risk: contract”: we need a trusted standard for a provider contract; “Loss of governance”: standards for provider certification and auditing required; “Privacy legislation”: standard how well a provider meets privacy laws; “Impersonation”: is user name/password sufficient?; “Insider abuse of privilege”, “Management Interface”; “Ineffective data deletion” ; “Poor authorization model”;
Mike Small also pointed out that current cloud provider assurance frameworks are far too complex with 148 control points. He introduced a star rating method scoring the major controls reducing the list to 5 basic and 11 risk factors.
In the evening Kuppinger and Cole presented the annual European Identity in several categories:
- Cloud provider offerings
- WSO2: multi tenant identity as a cloud service with OpenID and XACML support build on open source
- On premise to cloud migrations
- NHS Trust/ King’s College London: Secure infrastructures for researchers
- Identity and Access Management
- BrokerGate : Secure federation broker for insurance brokers to manage federations instead of managing all users
- Integrated identity & access management
- Telefonica O2 Czech Republic: successful deployment of a large scale IAM implementation covering provisioning, sso, audit, efficient application on-boarding and more
- GRC
- BT managed fraud reduction service: shared service providing real-time assessment of online transactions and analyzing fraud
- Privacy
- Qiy: Innovative approaches to manage the personal identity in the internet
- connect.me: recommendation network
- Identity related e-government project
- Postecom CECPAC: certified, free email platform open to all Italian citizens for their communications with public administrations
- Finland: Tunnistus.fi/KATSO: government to citizen/business services established in Finland now used by more than 70% of the Finnish companies
- Influential standardization efforts
- XACML 3.0: standard driving the externalization of security out of application for centralized management and control
- Special award entitlement management
- State of California: tax service based on external authentication and authorization using XACML 3.0
Day 3:
Three keynotes from Niels von der Hude, Beta Systems, Emilio Mordini, CEO of Centre for Science, Society and Citizenship, and Barbara Mandl from Daimler.
Mordini, a psychoanalyst, presented on the secrecy in the post wikileaks era. He elaborated the meaning of secrecy, s.th. hidden, kept separate from other things and invisible or unspoken. He asked the question: Do we still need secrecy in modern information society? His answer: we need secrecy and publicity and compared that to the life in a small village: everybody knows where you are, who you are what you are doing. But people do that with discretion: they pretend to ignore knowing the information. He concludes that ICT should address access rights. But strong data protection and security are often useless. True power is not to remember and to be remembered but forget and to be forgotten.
Back to reality: Barbara Mandl pointed towards the real problems a global corporation is confronted with. Data protection requirements in Germany, the US or Japan are total different. For example in Japan the working counsel supports to store and evaluate log in and log out times in active directory. Federation itself is not a solution as a whole. Contracts with every supplier and contracts for special applications pose challenges to legal departments. Both on Daimler and supplier side.
She also pointed out that things that work perfectly in private space, (e.g. security awareness in private online banking) due to protecting own belongings. But: the same people do not care about these things at work.
Legal track:
EIC offered a three hour crash course on international privacy and IT security law for IT professionals which compared the data protection legislation in the EU, the US and China and gave an introduction to the European legal requirements for data protection, IT security, encryption and audit. I remember a tweet saying: “It seems like two words can dissolve all the reputedly strong EU privacy & data security protections: contract or consent “. And that is exactly the point: opt-in rather than opt-out.
In another track on privacy Stephan Humer, Berlin University of Arts, presented on the sociological aspects of eID cards: technical people are problem centered. Normal people are not necessarily, they might act chaotic …
A talk from Maarten Wegdam, Novay, and a panel discussion analyzed topics like “Consumer and citizen identities; Governmental issued or trust frameworks? and “Identity assurance frameworks are now upon us. But what are they good for?”.
In the best practice track the winner of the EIC award “BrokerGate” reported from their project setting up a SAML identity provider service for 10.000 brokers and 20 insurer (final goal) in Switzerland with versatile authentication methods. In a final presentation Vassilia Orfanou from EUReID, the pan-european network of eID practitioners introduced the platform to consolidate documents and information, support networking and exchange of information related to eID projects in Europe: http://ePractice.eu.
Final words: a very successful conference and thanks to KuppingerCole for a perfect organization and composition of interesting topics. For interested readers: the European Identity Conference 2012 will be held on 17-20. April. So the fixed star has moved a little bit.